With the average data breach costing over $4.45 million, your greatest vulnerability is your own scattered, insecure documents.
Every file saved to a local desktop or shared in an email creates a security gap that invites compliance failures and costly mistakes.
A secure document management system replaces that chaos with a centralized fortress, using automation and enterprise-grade security.
What is Secure Document Management?
Secure document management is the practice of using a centralized system with specific technologies and policies to protect digital documents from creation to deletion.
It combines security features like end-to-end encryption, granular access control, and complete audit trails with automated workflows to keep your information protected from unauthorized access, data breaches, and compliance failures.
What Are the Risks of Insecure Document Management?
Before implementing a solution, you must assess your current risk profile. Insecure document handling leads to lost files and creates tangible financial and operational threats.
| Risk Factor |
Hidden Cost |
| Data Breaches |
A single compromised file can lead to millions in fines, legal fees, and reputational damage. |
| Compliance Failures |
Inability to produce auditable records for HIPAA, GDPR, or SOX can result in severe penalties. |
| Productivity Loss |
Teams waste countless hours searching for files or recreating work based on outdated versions. |
| Insider Threats |
Without granular permissions, disgruntled or careless employees can easily access or share sensitive data. |
| Business Continuity |
A localized disaster (fire, flood, or server failure) can wipe out your entire document archive if not properly backed up. |
How Does a DMS Protect Your Documents?

A modern DMS like Dokmee is engineered with overlapping layers of protection to safeguard your business and provide superior document management capabilities.
Granular Roles and Permissions
This features allows you to define exactly who can view, edit, print, share, or delete documents.
This is the first line of defense against both internal and external threats.
Dokmee enhances document security with features like dynamic watermarks and full restriction capabilities.
End-to-End Data Encryption
Data encryption converts your documents into a coded format (ciphertext) so it becomes unreadable to anyone who might intercept it without authorization.
Data is scrambled both “at rest” (on the server) and “in transit” (across the network).
This level of protection prevents unauthorized access from hackers, third parties, or even internal threats. It also ensures compliance with data privacy regulations like GDPR, HIPAA, and others.
A DMS that uses robust encryption protects sensitive documents from data breaches and builds trust by protecting your documents.
Unchangeable Audit Trails
Every action is accompanied by a detailed, time-stamped log that cannot be deleted or changed at any time.
You can see who viewed a file, what changes were made, and when. This provides full accountability for audits and facilitates compliance.
Automated File Retention Policies
Automatically enforce rules for file retention (how long documents are kept) and when they must be securely deleted to comply with regulations.
Automated Workflows
By automating your workflows, you can route documents for approval within a closed-loop system that will send notifications to involved team members at exactly the right time.
You can’t lose them in email or have them seen by the wrong people.
Flexible and Secure Deployment
Most modern DMS allow you to choose between on-premises, secure cloud, or hybrid models to meet specific IT governance and security requirements.
Dokmee offers you the flexibility of picking whichever implementation suits your business needs.
Centralized Version Control
Modern DMS automatically save a new version of a document every time it’s edited.
This preserves a full history and ensures everyone works from the master file, which drastically reduces the risk of working with outdated contracts or information.
Is a DMS More Secure Than Dropbox or Google Drive?
Yes, a DMS is much more secure than online document management tools.
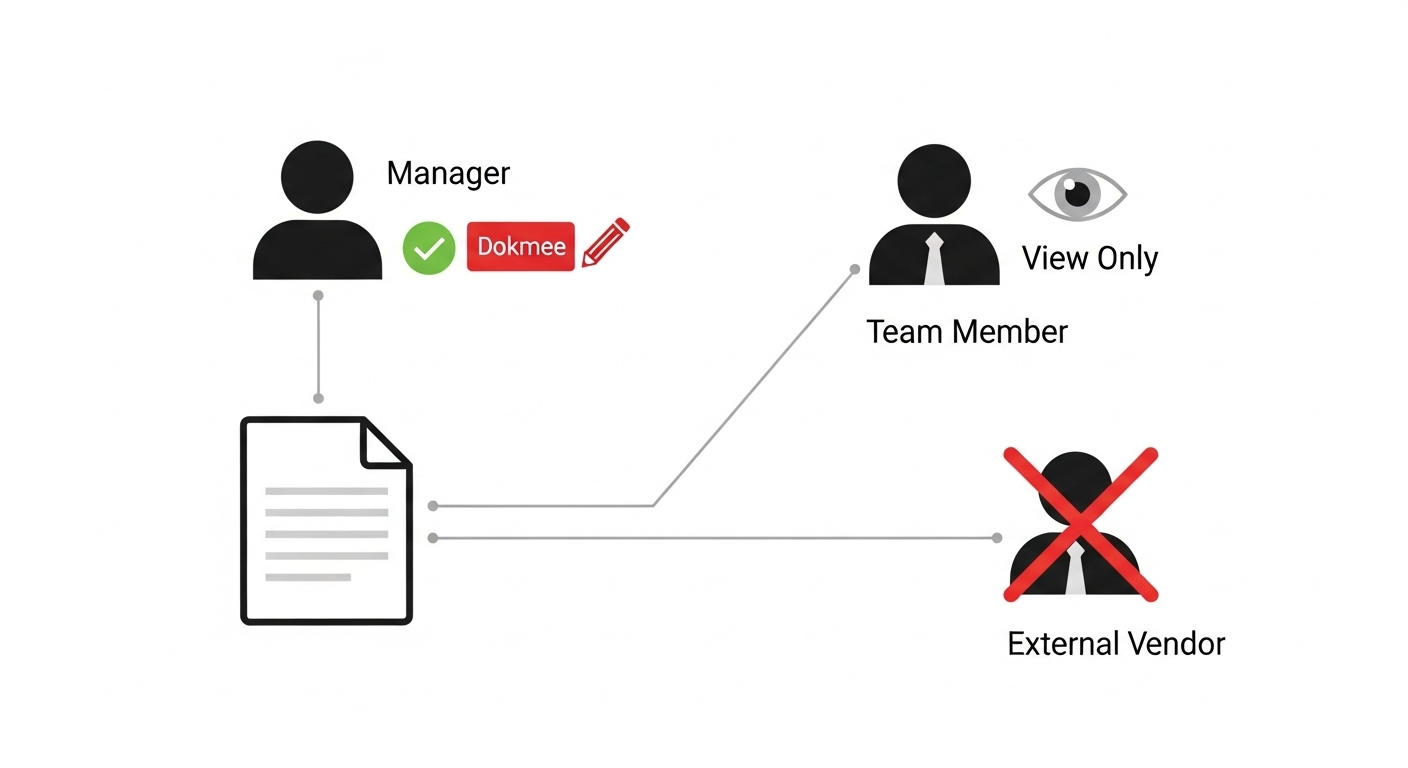
Many businesses mistakenly believe that standard cloud storage provides adequate security. This is not the case. While useful for simple sharing, these platforms lack the enterprise-grade architecture of a true DMS.
| Security Layer |
Standard Cloud Storage |
Dokmee DMS |
| Access Control |
Basic (viewer, commenter, editor) |
Advanced. Role-based, feature-based (print/no print), and data-level security. |
| Audit Trails |
Limited version history. Not compliance-grade. |
Complete and unchangeable. Logs every view, edit, and action for full accountability. |
| Automated Retention |
None. Manual deletion is required. |
Automated. Enforces company policies for document archival and disposal. |
| Secure Workflow |
None. Relies on manual sharing and email. |
Integrated and secure. Automates review and approval processes within the system. |
Ready to see the difference in a live environment? Request a Free Demo of Dokmee
Best Practices to Enforce Document Management Security
Technology is the foundation, but a secure culture is key. Here’s a checklist of the best practices for maintaining your documents’ security.
- Establish a clear security policy: Formally document your rules for data handling.
- Classify your data: Categorize documents by sensitivity (public, internal, confidential).
- Conduct regular employee training: Educate your team on risks like phishing.
- Implement the principle of least privilege: Give your employees the minimum access required to accomplish their tasks.
- Automate where possible: Use your DMS to automate workflows to reduce human error.
- Schedule regular security audits: Use the audit trail to review access logs.
- Secure your endpoints: Ensure all devices accessing the DMS are secure.
- Create a disaster recovery plan: DMS backups can secure business continuity in case of a catastrophic loss of data.
- Manage third-party access: Your vendors’ permissions should be strictly limited and temporary.
- Have a clear offboarding process: Immediately revoke all access for departing employees to prevent unauthorized access and reduce the risk of data leaks.
How Do You Implement a Secure Document Management System?
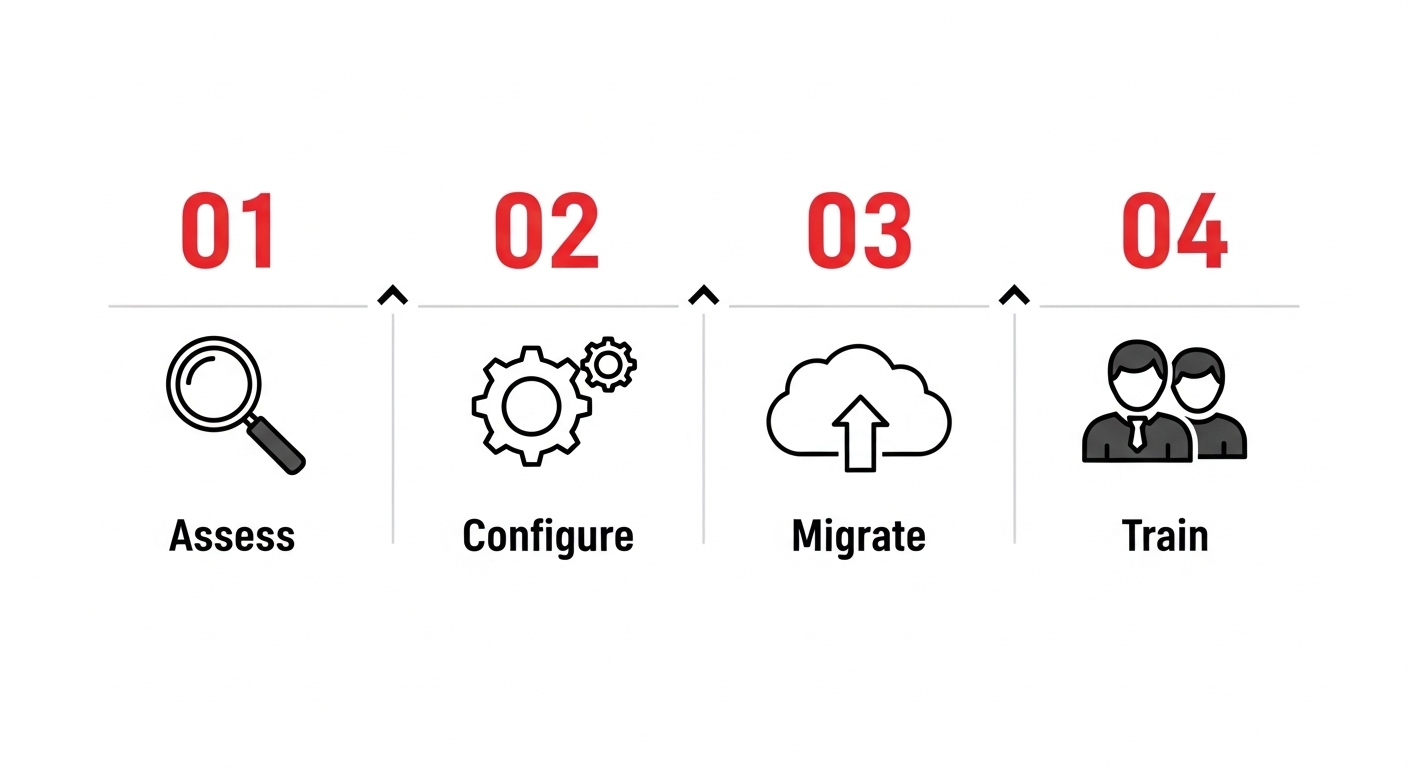
Implementing a secure DMS is a straightforward process. It breaks down into four logical steps. Here’s how you can ensure a smooth transition and maximize your return on investment.
1. Step 1: Assess and Plan
This foundational phase is about understanding your starting point and defining your destination.
Don’t rush this step, as it can lead to overlooking useful input from other team members, including your HR, legal, and compliance officer’s. This ensures the final system meets everyone’s needs.
Form a cross-functional team that includes leaders from IT, finance, HR, legal, and any other document-heavy departments.
Their combined perspective is necessary for ensuring the system meets the entire organization’s needs.
- Conduct a deep document audit
Go beyond just knowing where your files are.
You need to map the entire lifecycle. What types of documents do you handle (contracts, invoices, employee records)? Where are they currently stored? Who needs access, and at what stage? What are the current security gaps and compliance risks?
Translate your needs into specific, measurable objectives (KPIs).
Instead of a vague goal like “improve efficiency,” aim for “reduce invoice approval time by 50% within six months” or “achieve a 100% successful pass rate on all HIPAA document requests.”
2. Step 2: Configure the System
This is where you translate the policies and goals from your plan into the technical rules of your new DMS. A good provider will be a close partner during this phase.
- Design a logical structure
Create an intuitive folder structure (taxonomy) that makes sense for your business, typically organized by department, year, or project.
This ensures users can easily find what they need.
- Configure granular user roles
Go beyond "admin" and "user." Based on the Principle of Least Privilege, create specific roles like "Accounts Payable Clerk," who can upload and view invoices, while only a "Finance Manager" can approve payments.
This is the basis of your access control strategy.
Identify your most repetitive, high-volume processes and build automated workflows.
For example, a new contract can be automatically routed from Sales to Legal for review, then to the CEO for a signature. Simultaneously, configure retention policies to automatically archive or delete documents after their required lifespan.
3. Step 3: Digitize and Migrate
This phase involves moving your documents from their old, insecure locations into the new centralized fortress.
First, launch a pilot program. Don’t attempt a company-wide rollout on day one. Start with a single, high-impact department.
This pilot program will allow you to test your configuration, gather real-world feedback, and create a success story that builds momentum. It’ll also encourage adoption across the company.
Next, plan your migration strategy:
From a set "go-live" date, all new paper documents are scanned directly into the DMS.
Systematically scan your legacy documents from file cabinets. This can be done over time based on priority.
Plan the migration of existing electronic files from shared drives.
This is an opportunity to cleanse your data: delete duplicates and organize files before moving them into the new system to avoid a “garbage in, garbage out” scenario.
4. Step 4: Train and Adapt
A powerful system is only effective if people use it correctly. The final step is about change management and is necessary for maximizing your ROI.
- Provide role-based training
Don't give everyone the same training.
General users need to learn how to search and collaborate. Managers need to learn how to manage workflows and run reports. Administrators will need an explanation of the system's security settings.
- Explain why change is necessary
Explain why the new security policies are important and how the DMS will make employees' jobs easier by eliminating tedious tasks. This builds buy-in and reduces resistance to change
Manage Your Documents Securely with Dokmee
Protecting your information requires a capable, centralized system. A secure document management system like Dokmee provides the integrated features, automated policies, and complete auditability you need to operate with confidence.
Stop risking fines and data breaches. Secure your documents today.
Get Started with Dokmee
Frequently Asked Questions (FAQ)
What is a document management system?
A document management system (DMS) is a software solution used to capture, track, store, and manage electronic documents. Unlike simple cloud storage, a true DMS provides you with advanced features for security, version control, workflow automation, and compliance.
Is a DMS secure?
Yes. An enterprise-grade DMS is designed with security as its core foundation.
Systems like Dokmee offer multiple layers of protection, including data encryption, granular access controls, and complete audit trails. They’re more secure than standard file servers or cloud sharing platforms.
How do I know if my DMS enhances document management security?
A secure DMS will have specific, identifiable features. Look for role-based permissions, end-to-end encryption, automated retention policies, unchangeable audit logs, and features that support compliance with regulations like HIPAA or GDPR.
If your system lacks these, it’s not providing adequate security.
How to know if my DMS is secure?
Perform a quick check: Can you control who prints a specific document? Can you see a full history of every person who has viewed a file? Can you automatically delete contracts after 7 years?
If the answer to these questions is “no,” your DMS is likely not secure enough for business-critical documents.
Does Dokmee manage my document securely?
Absolutely.
Dokmee provides enterprise-grade security features, including 256-bit encryption, granular user and group permissions, dynamic watermarking, integration with Active Directory for access control, and a complete, unchangeable audit trail that logs every action for complete accountability and compliance.